Content
Examine Your Ports – test udp port
Open Up Slot Examine Device:
A port is an amount that embodies an access to a solution that levels to the network.
In computer networks, an open slot is actually a slot that currently utilizes (open) by a company. An available port can be actually utilized to send or/and receive records over the system.
- To scan individually, pick 'specific', input a valid port number, and pick 'Check'.
- You can likewise make use of the Neighbor Map as well as Course Viewer devices in ETS for a noticeable summary of just how your network is directing.
- With the SNMP MIB web browser, you can query SNMP-managed tools to check out configurations and also various other MIB characteristics.
- Network ports are the communication endpoints for an equipment that is linked to the Internet.
- Ports differ in their procedures and the sorts of services they supply.
TCP slots as well as UDP slots. Open slot check resource can inspect the condition of a TCP port.
An example can be your internet browser on the client-side and also an internet hosting server as the remote control server.
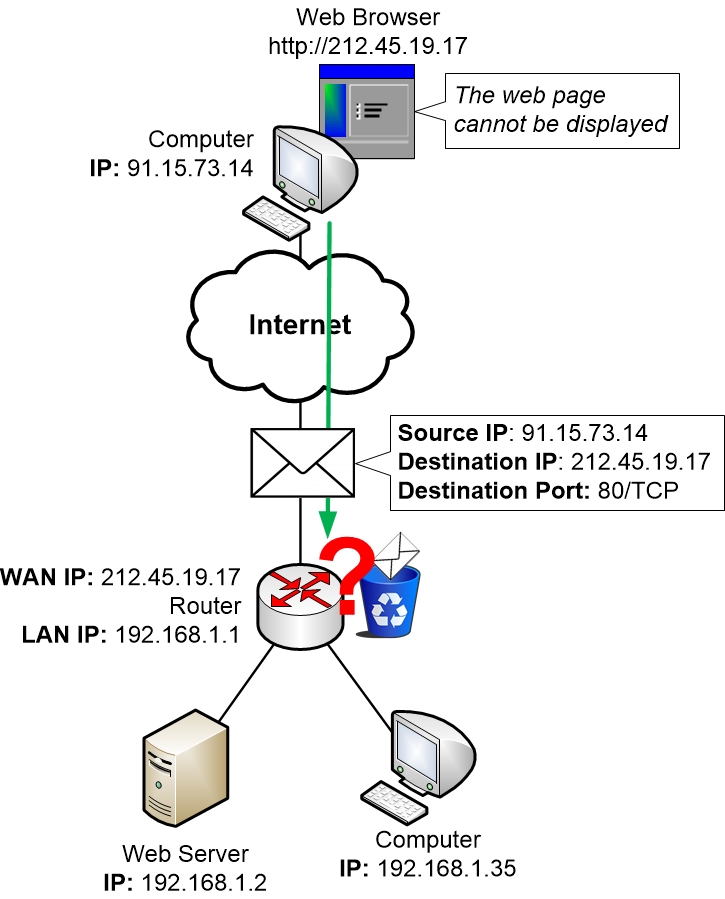
The internet server utilizes the nonpayment slot 80 for HTTP or even port 443 for HTTPS to pay attention and hang around for hookups. Your internet browser develops a relationship to that port, making use of a local slot. Once it connected they send out and also receive information between all of them. An available port inspection device can be used to examine if the port is actually currently available or certainly not on an intended device.
It feels like a port test, using this resource you can easily additionally identify slot forwarding condition.
If your web server is being actually blocked through a firewall, you can easily also utilize an available port inspection tool to remotely examine.
Port Scanner: A slot scanner is a device that may be made use of to scan a series of ports.
An additional sophisticated or even port checker can easily scan some deal with and even a complete network exploring for slots that level. In personal computer security and hacking it is extensively made use of to seek challenging open slots that intend to become close or monitor. An open slot resembles an open door or even a window. Along with the correct knowledge, it is actually achievable to use this slot to get in into the remote control computer system.
Utilizing as well as operating a normal slot scan is actually a really good strategy to locate available ports and shut all of them. If an open port is actually found it is likewise made use of to understand why and also that open it.
What Is A Port Scanner? – port checker
There are actually some extremely helpful tools that can easily be utilized to check the system address for open ports. Utilizing such tools can easily even discover deal with inside the association that needs to have to be actually cleared away.
An instance of system slots scanner resource is actually Nmap. Utilizing it you may browse full subnet. It sustains numerous browse techniques like TCP SYN check and also TCP ACK browse. Advanced usage of the device can easily locate what is the solution (procedure) that open up the port and the operating device behind this service.
On the internet port scanning device:
The outdated craft of port scanning is still functioning. Also thou that today there is actually a more secure approach to shut and also track ports and solutions in the functioning atmosphere.
. A Breach detection system (IDS) could be utilized to observe the system.
Along with the advanced of new tools, an on-line slot scanning device tool may be used as a source to browse a setting. Browsing coming from outside the organization.
An on the internet port scanner is a slot scanning device like some other slot scanning device. The only deferent is actually that it works from outside your network. re: an internet site-- online.
If you possess excessive available slots on your computer/device that needs to have to be actually finalized, it is actually a great tool that can be used to check.
Solutions that rely upon the Net (like internet internet browsers, internet webpages, as well as documents transactions companies) count on details slots to acquire and also broadcast details. Creators make use of report transactions methods () or even SSH to operate encrypted passages around pcs to discuss details in between multitudes.
When a solution is operating on a certain port, you can't run other companies on it. read more For instance, beginning Apache after you've presently started Nginx on slot 80 will certainly result in a failed operation because the port is already in make use of.

Open slots become hazardous when reputable services are actually capitalized on through surveillance susceptibilities or even harmful solutions are introduced to a system using malware or even social design, cybercriminals can easily utilize these services combined with available slots to acquire unauthorized access to sensitive records.
Closing remaining slots minimizes your safety and security risk through lessening the lot of assault vectors your organization is actually left open to.